Overview
Sometimes you need to make a quick decision about a system or systems and don't have the time or resources to make full images. For example, during a knock and talk you want to know if there is notable data on their system. Or you are at a location with many systems and want to know which should be analyzed first. Autopsy has features that will allow you to quickly find the data of interest without making full images of the devices. Those features will be described below, followed by some example scenarios that show how to put everything together.
Triage-related Features
There are many features of Autopsy that can come into play in a triage situation. Some help you process the files most likely to be relevant earlier, and others allow you to continue analyzing the data after disconnecting from the target system.
Prioritization
The goal is to find the most important files first when there is limited time to analyze a system. Autopsy always runs on the user folders first (if present), since in many situations they are the most likely folders to contain data of interest.
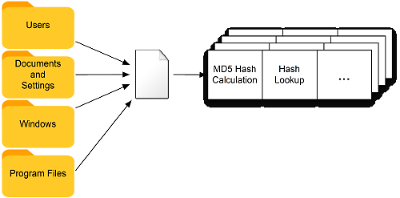
File Filters
For a particular scenario, you may know specific file types that you are interested in. For example, if you are only concerned with finding images, you could save time by not analyzing any non-image files. This will allow a system to be processed far faster than if you analyzed every file.
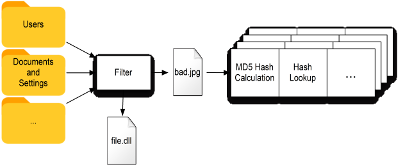
File filters allow you to limit which types of files will be processed. The Custom File Filters section of Ingest Modules page shows how to create a file filter. You can filter on file name/extension, path, or how recently the file was modified. Once saved, your new file filter can be selected when configuring ingest modules.
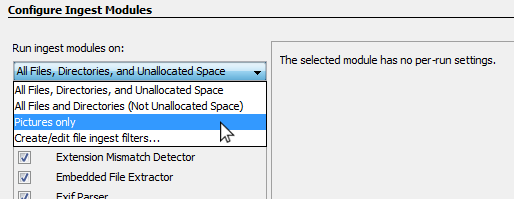
Ingest Profiles
Another way to speed up analysis is to only run some of the ingest modules. For example, if we're only interested in images, there may be no point in running the Keyword Search Module or the Encryption Detection Module. You can manually select and configure the modules you want to run each time, but since many sessions are similar it may be easier to set up an ingest profile. An ingest profile allows you to store which file filter you want to run, which ingest modules should be enabled, and your configuration for each ingest module.
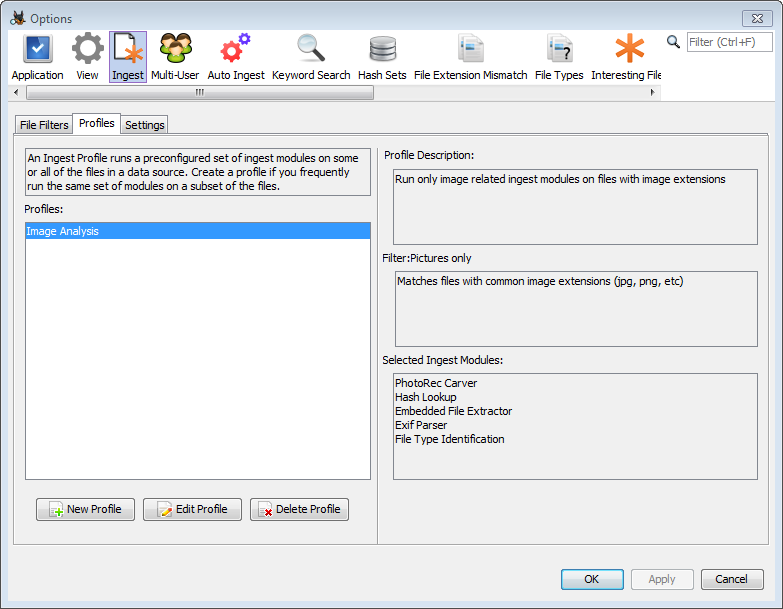
Once you have at least one ingest profile configured, a new screen will appear before the normal ingest module configuration panel. If you choose your user-defined profile, that ingest module configuration panel will be skipped entirely and the ingest modules from that profile will be run on the data source.
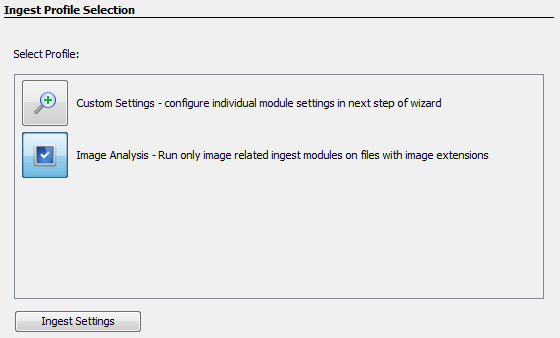
See the Using Ingest Profiles section of the Ingest Modules page for additional information on how to set up and use an ingest profile.
Running on Live Systems and Devices
In a triage situation, there is generally not time to make a full image of the system in question. There are a few ways to process live systems and devices with Autopsy:
- Devices such as USB drives can be analyzed as local disks without needing to create an image file. See the Adding a Local Disk section for more details.
- A live triage drive can be created that will allow you to run Autopsy from a USB drive on a live system. All case data will be saved to the USB drive with minimal changes to the system being analyzed. See Creating a Live Triage Drive for more details.
- The target computer can be booted from a trusted Linux or Windows USB and Autopsy can be run from it. Paladin includes Autopsy in its bootable Linux USB and a Windows FE image can be created as well.
Making a Sparse Image
With any of the above methods for analyzing live systems and devices there is still the problem that your Autopsy case won't be very useful after you disconnect from the drive. It will refer to a device that no longer exists and, more importantly, you may not have a copy of any files of interest that you observed during the triage.
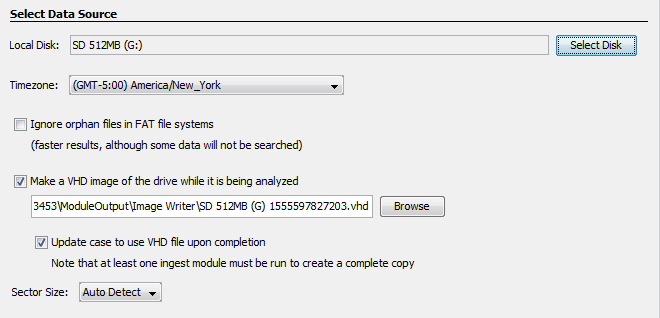
To solve this problem you can choose to make a "sparse VHD" as Autopsy is processing the device. This will save a copy of every sector that Autopsy reads, which will include file system structures (such as Master File Tables) and files that passed the ingest filters (such as all pictures).
VHD is a file format used by Microsoft Virtual Machines that is readable by Windows and other forensic tools. The VHD will grow in size as Autopsy reads more data from the target drive.
To create a sparse VHD, check the box for "Make a VHD image..." when selecting the disk to analyze.
Scenarios
Scenario: Previewing computer for child exploitation material
In this scenario, you are trying to answer whether child exploitation images exist in a knock and talk type situation where you will have a limited amount of time with the target system.
Preparation at the office:
- Create a live triage drive on your USB drive
-
Launch Autopsy from that USB drive and create an ingest profile that:
- Uses a file filter that runs on only picture and ZIP extensions
- Runs only the Hash Lookup Module, EXIF Parser Module File Type Identification Module, and Embedded File Extraction Module
- Uses known child exploitation hash sets, following the instructions in Using hash sets to copy them to the USB drive
At the house:
-
Start the analysis:
- Plug the live triage drive you made at the office into their laptop
- Launch Autopsy from the .bat file
- Create a case (saving to your USB drive)
-
Add a local drive data source
- "C:"
- Choose to make VHD and keep default location
-
As the automated analysis continues:
- Choose View->File Types->Images in the tree viewer and review the thumbnails
- Wait for hash set hits
- Review EXIF fles
- Tag any notable files found
- You can stop the analysis at any time. All data read so far will be in the VHD file.