What Does It Do
The Embedded File Extractor module opens ZIP, RAR, other archive formats, Doc, Docx, PPT, PPTX, XLS, and XLSX and sends the derived files from those files back through the ingest pipeline for analysis.
This module expands archive files to enable Autopsy to analyze all files on the system. It enables keyword search and hash lookup to analyze files inside of archives
NOTE: Certain media content embedded inside Doc, Docx, PPT, PPTX, XLS, and XLSX might not be extracted.
Configuration
There is no configuration required.
Using the Module
Select the checkbox in the Ingest Modules settings screen to enable the Archive Extractor.
Ingest Settings
There are no runtime ingest settings required.
Seeing Results
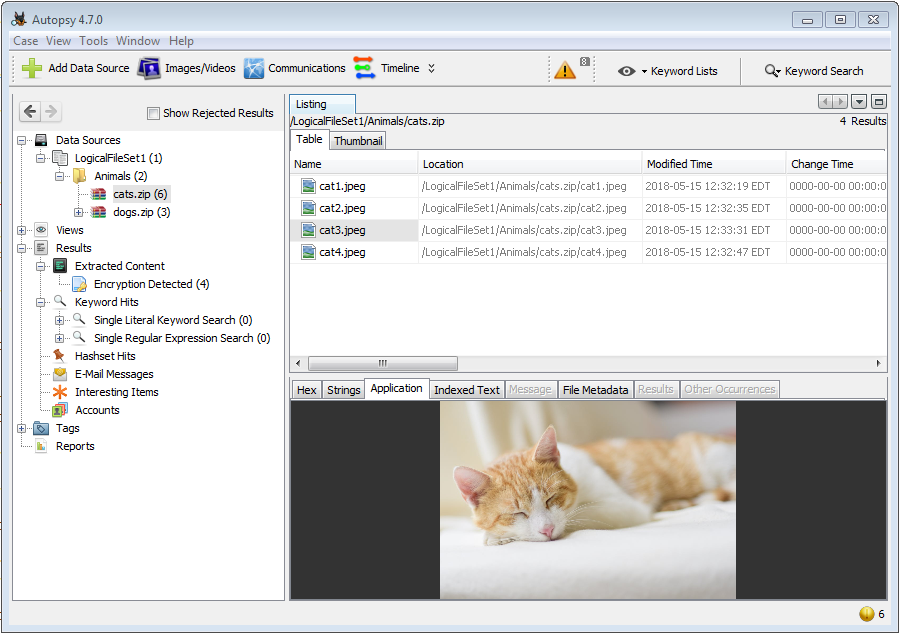
Each file extracted shows up in the data source tree view as a child of the archive containing it,
and as an archive under "Views", "File Types", "Archives".
Encrypted Archives
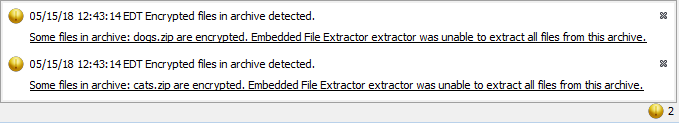
When the Embedded File Extractor module encounters an encrypted archive, it will generate a warning bubble in the bottom right of the main screen:
After ingest, you can attempt to decrypt these archives if you know the password. Find the archive (either in the tree view or result view) and right-click on it, then select "Unzip contents with password".
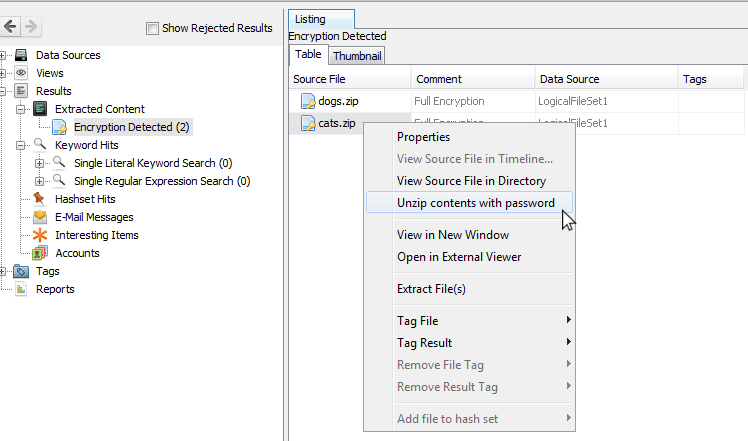
After entering the password, you can select which ingest modules to run on the newly extracted files. When finished, you can browse to the encrypted archive in the tree view to see the newly extracted files. If the archive was already open in the tree, you may have to close and open the case in order to see the new data.